$whoami
I am a Security Engineer at AWS, with a Ph.D. in Computer Engineering from Virginia Tech. My foundational expertise lies in securing embedded systems, analyzing side channels, and designing defenses at the silicon and platform levels.
Lately, I’ve been exploring how those hardware trust anchors scale and integrate into larger cloud ecosystems—how attestation, key management, and system firmware interact in the broader service stack. My work aims to bridge the design gap between physical security and cloud trust boundaries, so that secure architecture can flow smoothly from silicon to service.
Specialties & Interests:- Hardware and firmware trust and isolation
- Side-channel analysis, device aging, power/EM leakage
- Secure provisioning and anti-counterfeit trust schemes
- Interfaces between platform security and cloud-based attestation
- Applied cryptographic primitives in hardware-constrained contexts
$man education
- Ph.D., Computer Engineering'24, Virginia Tech
Advisor: Dr. Matthew Hicks - M.S., Electrical & Computer Engineering'19, Auburn University
Thesis: Towards Unclonable System Design for Resource-constrained Applications.
Advisor: Dr. Ujjwal Guin - B.S., Electrical & Electronic Engineering'16, BUET
Thesis: Metal-Insulator-Metal Ring Resonator for Sensing Applications.
$ls -lt publications
- Jubayer Mahmod and Matthew Hicks. SRAM Has No Chill: Exploiting Power Domain Separation to Steal On-Chip Secrets. (Communications of the ACM- Research Highlights, July 2025)
- Jubayer Mahmod and Matthew Hicks. PhasePrint: Exposing Cloud FPGA Fingerprints by Inducing Timing Faults at Runtime. (ASPLOS 2025)
- Jubayer Mahmod and Matthew Hicks. UnTrustZone: Systematic Accelerated Aging to Expose On-chip Secrets. IEEE Security and Privacy (SP2025)
- Jubayer Mahmod and Matthew Hicks. SRAM Imprinting for System Protection and Differentiation. ACM ASIA Conference on Computer and Communications Security (AsiaCCS'24)
- Jubayer Mahmod and Matthew Hicks. Invisible Bits: Hiding Secret Messages in SRAM’s Analog Domain. International Conference on Architectural Support for Programming Languages and Operating Systems (ASPLOS). March 2022.
- Jubayer Mahmod and Matthew Hicks. SRAM Has No Chill: Exploiting Power Domain Separation to Steal Onchip Secrets. International Conference on Architectural Support for Programming Languages and Operating Systems (ASPLOS). March 2022.
- Jubayer Mahmod, and Ujjwal Guin. "A Robust, Low-Cost and Secure Authentication Scheme for IoT Applications." Cryptography 4.1 (2020): 8.
- Jubayer Mahmod, Millican Spencer, Ujjawal Guin, and Vishwani Agrawal. "Delay Fault Testing: Present and Future" Embedded tutorial, VTS 2019
- Benjamin Cyr, Jubayer Mahmod, Ujjwal Guin. "Low-Cost and Secure Firmware Obfuscation Method for Protecting Electronic Systems from Cloning" IEEE Internet of things Journal 2019.
- Jubayer Mahmod, Rakib Hyder, and Md Zahurul Islam. A Highly Sensitive Metal-Insulator-Metal Ring Resonator-Based Nanophotonic Structure for Biosensing Applications. "IEEE Sensors Journal (2018). [Note: undergraduate thesis]
- Jubayer Mahmod, Rakib Hyder, and Md Zahurul Islam. "Numerical studies on a plasmonic temperature nanosensor based on a metal-insulator-metal ring resonator structure for optical integrated circuit applications." Photonics and Nanostructures-Fundamentals and Applications 25 (2017): 52-57. [Note: undergraduate thesis]
Selected Projects
UnTrustZone
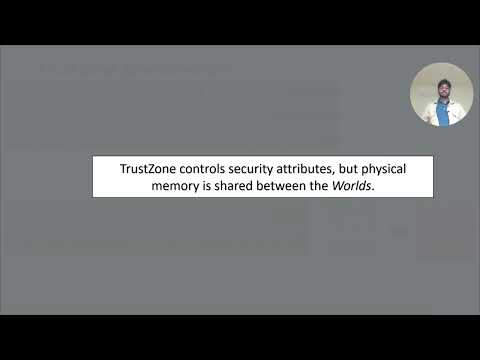
This project shows how long-term-data remanence is a threat to Trusted Execution System such as ARM TrustZone.
.jpg)

Voltboot
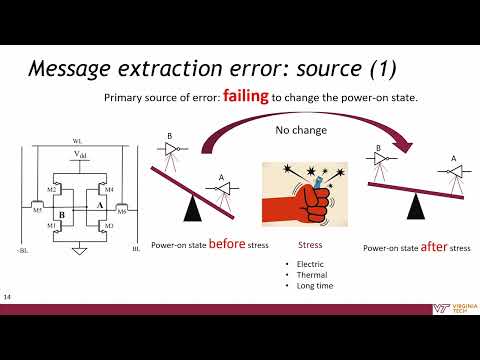
Creating artificial data retention in on-chip SRAM cell. This is a cold-style attack on on-chip SRAM, but without any cooling effect needed
Invisible Bits
This project is designed to conceal information in the analog layer of static random access memories (SRAM) with plausible deniability. The idea is to burn data into the transistor so that it is reflected in the SRAM's power-on state. The hidden information coexists with the data in the digital layer. That is, the system shows no signs of hidden data anywhere.


Cloud FPGA localization
Cloud service providers typically restrict access to low-level device information, such as device DNA. This project introduces an RTL design that utilizes the FPGA clock synthesizer to extract device behavior, enabling identification of specific FPGAs in the cloud. The system includes a hardware/software suite for seamless integration with AWS F1 instances, featuring necessary RTL and system service modules for signature extraction during the boot phase of the host CPU.
Reviewer
- Reviewer: ICCD'24
- IEEE Internet of Things Journal'22
- Subreviewer: IEEE Transactions on Circuits and Systems I'21 VLSID'19 DAC'19 GLSVLSI'19, Journal of Hardware and Systems Security'19 IEEE Transactions on Very Large Scale Integration Systems'17 &'18 VLSI Test Symposium'18 Transactions on Multi-Scale Computing Systems'18
Awards
- Communications of the ACM: Research Highlights 2025
- Security dissertation award (HOST) finalist'2024
- Graduate school tuition fellowship 2017-19 (MS in Auburn University).
- Best project award Tensilica Xtensa Embedded-DSP design contest 2016 (Organized by Cadence).
- Dean's list award and merit list award (BUET).